Since the outbreak of Petya/NotPetya which was surfaced in the month of June, again last week a new ransomware attack “aka BadRabbit” is making the headlines effecting machines in Ukraine, Russia, Turkey and Bulgaria.
Initial Attack Vector:
Unlike Petya/NotPetya that use SMB (Eternal Blue) as the initial vector, this variant uses drive-by-download type of attack to deliver the malware (BadRabbit) that spreads via malicious websites.
BadRabbit utilizes:
- Diskcryptor to encrypt the files with selected extensions
- SCmanager, schtasks and rundll32.exe to invoke other components
- For lateral movement, it scans the local networks for SMB shares and spread via SMB
- Mimikatz for credential harvesting on compromised machine
Analyzed samples:
| MD5 Hash | Description |
|---|---|
| fbbdc39af1139aebba4da004475e8839 | Adobe_Flash_Update – Dropper |
| 1d724f95c61f1055f0d02c2154bbccd3 | infpub.dat – Main DLL |
| b4e6d97dafd9224ed9a547d52c26ce02 | cscc.dat – Driver for Encryption |
| b14d8faf7f0cbcfad051cefe5f39645f | dispci.exe – DiskCryptor Client |
Behavioral analysis:
Once downloaded, the executable dropper pretending to an Adobe Flash Update convincing the victim to install it
Upon execution it drops the main module DLL “infpub.dat” in “C:\Windows” directory that is further initiated by rundll.exe with arguments.
C:\Windows\system32\rundll32.exe C:\Windows\infpub.dat,#1 15
Executes the command “schtasks /Delete /F /TN rhaegal” to delete any existing tasks with name “rhaegal”.
During the execution of main DLL “infpub.dat” other components (cscc.dat, dispci.exe) responsible for encrypting are being dropped.
To launch the newly dropped components of diskcryptor “dispci.exe” on the startup, a new task is scheduled with name “rhaegal”.
New service named “cscc” is created for DiskCryptor Driver “cscc.dat”.
ServiceName=cscc,DisplayName=Windows Client Side Caching DDriver, BinaryPathName=cscc.datSchedules a task named “drogon” to forcefully reboot the machine at 04:46hrs, it appears that a reboot is required to install the DiskCryptor drivers.
BadRabbit encrypts only selected file extension as below and displays a ransom note.
3ds, 7z, accdb, ai, asm, asp, aspx, avhd, back, bak, bmp, brw, c, cab, cc, cer, cfg, conf, cpp, crt, cs, ctl, cxx, dbf, der, dib, disk, djvu, doc, docx, dwg, eml, fdb, gz, h, hdd, hpp, hxx, iso, java, jfif, jpe, jpeg, jpg, js, kdbx, key, mail, mdb, msg, nrg, odc, odf, odg, odi, odm, odp, ods, odt, ora, ost, ova, ovf, p12, p7b, p7c, pdf, pem, pfx, php, pmf, png, ppt, pptx, ps1, pst, pvi, py, pyc, pyw, qcow, qcow2, rar, rb, rtf, scm, sln, sql, tar, tib, tif, tiff, vb, vbox, vbs, vcb, vdi, vfd, vhd, vhdx, vmc, vmdk, vmsd, vmtm, vmx, vsdx, vsv, work, xls, xlsx, xml, xvd, zipAbuse use of APIs:
CloseHandle CreateFileW CreateProcessW ExitProcess GetCommandLineW GetCurrentProcess GetFileSize GetModuleFileNameW GetModuleHandleW GetSystemDirectoryW HeapAlloc ReadFile TerminateProcess UnhandledExceptionFilter WriteFile
URL Found:
http://rb.symcb.com/rb.crl0W http://s.symcb.com/universal-root.crl0 http://ocsp.verisign.com0 https://www.verisign.com/rpa https://www.verisign.com/rpa0 http://rb.symcb.com/rb.crt0 http://ts-crl.ws.symantec.com/sha256-tss-ca.crl0 https://d.symcb.com/cps0% http://s.symcd.com06 http://crl.verisign.com/pca3-g5.crl04 http://ts-ocsp.ws.symantec.com0; https://d.symcb.com/rpa0@ https://d.symcb.com/rpa0 https://www.verisign.com/cps0 https://d.symcb.com/rpa06 http://crl.thawte.com/ThawteTimestampingCA.crl0 http://s.symcd.com0 http://ocsp.thawte.com0 https://d.symcb.com/rpa0. http://rb.symcd.com0& http://ts-crl.ws.symantec.com/tss-ca-g2.crl0( http://sf.symcb.com/sf.crt0 http://ts-aia.ws.symantec.com/sha256-tss-ca.cer0( http://logo.verisign.com/vslogo.gif04 http://sf.symcd.com0& http://ts-aia.ws.symantec.com/tss-ca-g2.cer0< http://sf.symcb.com/sf.crl0W http://ts-ocsp.ws.symantec.com07
Lateral Movement:
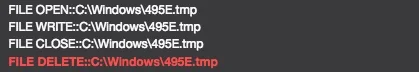
To perform credential harvesting, it creates and loads mimikatz to a file with extension “.tmp” (xxxx.tmp) in “C:\Windows\” and initiates a new process from the temp file “495E.tmp” with pipe.
Notice that the malware scans the local network for ports 139, 445 and spreads via SMB shares with credentials harvested using mimikatz.
- Praveen Kolanuvada